So I have decided that installing VMware is best solution.
Becuase disk space is not enough in my toshiba 5100, windows 98 SE was chosen for guest OS.
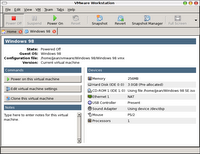 And installed a nortel extranet 2.56, installing looks fine but failed with error.
And installed a nortel extranet 2.56, installing looks fine but failed with error.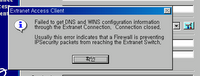
 Error message saying " Your IPsec tunneling have some problem."
Error message saying " Your IPsec tunneling have some problem."to enable IPsec on Vmware NAT another hundreds of searching was done.
Of cource it was ended with fail.
So I decide to find a VPN client for linux.
Because I don't have Nortel's VPN Client - provided with VPN switch-, have to find a freeware.
First I found "pptp"
apt-get install pptp
to configure this, also installed "pptpconfig"
add following on /etc/apt/sources.list
# James Cameron's PPTP GUI packaging deb http://quozl.netrek.org/pptp/pptpconfig ./
apt-get install pptpconfig
and, start the 'pptpconfig' and add the host.
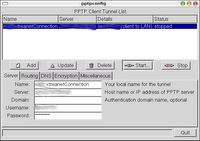 failed again.
failed again.And Found anotheroption, OpenSwan(www.openswan.org) will make a ipsec tunneling in linux.
apt-get install openswan.
it's installed greatly and ipsec command runs fine.
but I didn't find a way to connect VPN.
So have decided to install a cisco vpn client which use a same ipsec protocol.
followings are from http://www.mcmaster.ca/uts/network/vpn/vpnclient_linux.htm
Below is a quick installation and configuration guide for the Linux Cisco VPN client. For more in depth instructions, please refer to the Cisco documentation linked below.
Before you Begin...- This software and guide is unsupported by University Technology Services. This means that the installation and software has been tested by UTS, but no telephone support is available.
- The VPN client consists of a kernel module and a few command-line executables.
- The kernel module is not pre-compiled, so you may need to make sure that kernel sources for each kernel version that you are intending to use with this client are properly installed.
- To do this, find either the kernel source or header RPM from your installation cdroms. The most likely location is one of the RPMxx directories on one of the installation CD's. On Mandrake 9.2, it's called kernel-source-2.4.22-10mdk.i586.rpm, on Redhat 9.0 it's called kernel-source-2.4.20-8.i386.rpm. The kernel revision numbers change but you get the idea. Older versions of Linux may have just the kernel-header RPM.
- Install the RPM (rpm -i kernel-source-xxxxxx.rpm)
- The module is not Open Source Software, so after it's loaded into your Linux kernel, the kernel will become tainted, and will issue a warning.
- After successfully establishing a secure connection to the server, the client will listen for packets from the VPN server on 2 ports,UDP 500 and UDP 4500, by default. This means you have to punch a hole in your ipchains/iptables firewall for it. The module will also use IP protocol 50 (ESP) to communicate with the VPN server. That protocol is not filtered by most Linux firewall configurations, however.
- The CISCO documentation mentions several other ports, quoting:
- UDP port 500
- UDP port 10000 and 500 (or any other port number being used for IPSec/UDP)
- IP protocol 50 (ESP)
- NAT-T port 4500 UDP
- On our test systems, it appears that the VPN client will not work, when the operating system is running in "Security Enhanced" mode (SELinux). We suggest that you not run the system in this mode, if you plan on using the vpn client. To do this, cd to the /etc/selinux folder ... then edit the config file as follows (change "enforcing" to "disabled"). In this example, it's simply been commented out:
[root@linuxbox selinux]# more config
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - SELinux is fully disabled.
#SELINUX=enforcing
SELINUX=disabled
# SELINUXTYPE= type of policy in use. Possible values are:
# targeted - Only targeted network daemons are protected.
# strict - Full SELinux protection.
SELINUXTYPE=targeted
[root@linuxbox selinux]# - Become super user (root): [user@vpnclient]$ su -
- Change directory to /usr/src: [root@vpnclient root]# cd /usr/src
- Download the tar ball from the University web site: [root@localhost root]# wget http://www.mcmaster.ca//uts/network/software/vpnclient4.8.tar.gz
- Decompress and extract it: [root@vpnclient src]# tar xzvf vpnclient4.8.tar.gz
- Change directory to /usr/src/vpnclient: [root@vpnclient src]# cd vpnclient
- Execute the installer script and answer the prompts: [root@localhost vpnclient]# ./vpn_install
- Load the VPN client's module into the running kernel:
- At this point, we recommend that you restart the operating system ... otherwise, you may get the following message, when invoking the vpnclient: vpnclient: error while loading shared libraries: /opt/cisco-vpnclient/lib/libvpnapi.so: cannot restore segment prot after reloc: Permission denied
- McMaster VPN requires a profile to connect. Two are provided, one for off campus users (McMasterVPN) and one for on campus MacConnect users (MacConnect).
- The profiles are already installed in /etc/CiscoSystemsVPNClient/Profiles/:
- To connect, enter your user name and password when prompted:
- Note: If you open up another terminal window, and type "ifconfig" you should see - as well as the settings for your network interface, eth0 - another interface listed: "cipsec0" - this is the vpnclient interface. Its IP Address will be listed as well.
- You should now be connected to the McMaster network. If the connection fails, suspect your firewall first. Try disabling it completely then try the connection again! If the firewall interferes with the VPN, you will need to adjust its configuration.
- Use the vpn_uninstall script that comes with the client (/usr/src/vpnclient/vpn_uninstall in our example) to remove the client.
Installation and Configuration Commands, Step by Step
Below are step by step quick-start instructions. Be sure to connect to your ISP before starting.
This client has been tested on systems running Fedora Core 4.
[root@linuxbox ~]# uname -a Linux linuxbox.whatever.mcmaster.ca 2.6.11-1.1369_FC4 #1 Thu Jun 2 22:55:56 EDT 2005 i686 i686 i386 GNU/Linux
Password: {root's password}
[root@vpnclient root]#
--09:59:22-- http://www.mcmaster.ca//uts/network/software/vpnclient4.8.tar.gz => `vpnclient4.8.tar.gz'
Resolving www.mcmaster.ca... 130.113.64.65
Connecting to www.mcmaster.ca[130.113.64.65]:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2,050,187 (2.0M) [application/x-tar]
100%[===============================================>] 2,050,187 10.02M/s 09:59:22 (10.02 MB/s) - `vpnclient4.8.tar.gz' saved [2050187/2050187]
Length: 2,811,577 [application/x-tar]
100%[====================================>] 2,811,577 9.31M/s 10:55:29 (9.31 MB/s) - `vpnclient-linux4.7.tar.gz' saved [2,811,577/2,811,577]
vpnclient/
vpnclient/linux_os.h
vpnclient/IPSecDrvOS_linux.c
vpnclient/mtu.h
vpnclient/linuxkernelapi.c
vpnclient/vpnapi.h
vpnclient/libdriver64.so
vpnclient/license.txt
vpnclient/sample.pcf
vpnclient/cvpnd
vpnclient/interceptor.c
vpnclient/unixcniapi.h
vpnclient/MacConnect.pcf
vpnclient/Makefile
vpnclient/GenDefs.h
vpnclient/libdriver.so
vpnclient/config.h
vpnclient/vpn_uninstall
vpnclient/McMasterVPN.pcf
vpnclient/vpnclient_init
vpnclient/IPSecDrvOS_linux.h
vpnclient/cisco_cert_mgr
vpnclient/Cniapi.h
vpnclient/vpnclient
vpnclient/libvpnapi.so
vpnclient/unixkernelapi.h
vpnclient/ipseclog
vpnclient/IPSecDrvOSFunctions.h
vpnclient/linuxcniapi.c
vpnclient/license.rtf
vpnclient/vpn_install
vpnclient/driver_build.sh
vpnclient/vpnclient.ini
vpnclient/frag.c
vpnclient/linuxcniapi.h
vpnclient/frag.h
vpnclient/vpn_ioctl_linux.h
Cisco Systems VPN Client Version 4.8.00 (0490) Linux Installer
Copyright (C) 1998-2005 Cisco Systems, Inc. All Rights Reserved.
By installing this product you agree that you have read the
license.txt file (The VPN Client license) and will comply with
its terms.
Directory where binaries will be installed [/usr/local/bin]
Automatically start the VPN service at boot time [yes]
In order to build the VPN kernel module, you must have the
kernel headers for the version of the kernel you are running.
Directory containing linux kernel source code [/lib/modules/2.6.16-1.2111_FC4/build]
* Binaries will be installed in "/usr/local/bin".
* Modules will be installed in "/lib/modules/2.6.16-1.2111_FC4/CiscoVPN".
* The VPN service will be started AUTOMATICALLY at boot time.
* Kernel source from "/lib/modules/2.6.16-1.2111_FC4/build" will be used to build the module.
Is the above correct [y] y
Making module
make -C /lib/modules/2.6.16-1.2111_FC4/build SUBDIRS=/usr/src/vpnclient modules
make[1]: Entering directory `/usr/src/kernels/2.6.16-1.2111_FC4-i686'
CC [M] /usr/src/vpnclient/linuxcniapi.o
CC [M] /usr/src/vpnclient/frag.o
CC [M] /usr/src/vpnclient/IPSecDrvOS_linux.o
CC [M] /usr/src/vpnclient/interceptor.o
/usr/src/vpnclient/interceptor.c: In function ‘handle_vpnup’:
/usr/src/vpnclient/interceptor.c:310: warning: assignment from incompatible pointer type
/usr/src/vpnclient/interceptor.c:334: warning: assignment from incompatible pointer type
/usr/src/vpnclient/interceptor.c:335: warning: assignment from incompatible pointer type
/usr/src/vpnclient/interceptor.c: In function ‘do_cleanup’:
/usr/src/vpnclient/interceptor.c:378: warning: assignment from incompatible pointer type
CC [M] /usr/src/vpnclient/linuxkernelapi.o
LD [M] /usr/src/vpnclient/cisco_ipsec.o
Building modules, stage 2.
MODPOST
Warning: could not find /usr/src/vpnclient/.libdriver.so.cmd for /usr/src/vpnclient/libdriver.so
CC /usr/src/vpnclient/cisco_ipsec.mod.o
LD [M] /usr/src/vpnclient/cisco_ipsec.ko
make[1]: Leaving directory `/usr/src/kernels/2.6.16-1.2111_FC4-i686'
Create module directory "/lib/modules/2.6.16-1.2111_FC4/CiscoVPN".
Copying module to directory "/lib/modules/2.6.16-1.2111_FC4/CiscoVPN".
Already have group 'bin'
Creating start/stop script "/etc/init.d/vpnclient_init".
/etc/init.d/vpnclient_init
Enabling start/stop script for run level 3,4 and 5.
Creating global config /etc/opt/cisco-vpnclient
Installing license.txt (VPN Client license) in "/opt/cisco-vpnclient/":
Installing bundled user profiles in "/etc/opt/cisco-vpnclient/Profiles/":
* New Profiles : MacConnect McMasterVPN sample
Copying binaries to directory "/opt/cisco-vpnclient/bin".
Adding symlinks to "/usr/local/bin".
/opt/cisco-vpnclient/bin/vpnclient
/opt/cisco-vpnclient/bin/cisco_cert_mgr
/opt/cisco-vpnclient/bin/ipseclog
Copying setuid binaries to directory "/opt/cisco-vpnclient/bin".
/opt/cisco-vpnclient/bin/cvpnd
Copying libraries to directory "/opt/cisco-vpnclient/lib".
/opt/cisco-vpnclient/lib/libvpnapi.so
Copying header files to directory "/opt/cisco-vpnclient/include".
/opt/cisco-vpnclient/include/vpnapi.h
Setting permissions.
/opt/cisco-vpnclient/bin/cvpnd (setuid root)
/opt/cisco-vpnclient (group bin readable)
/etc/opt/cisco-vpnclient (group bin readable)
/etc/opt/cisco-vpnclient/Profiles (group bin readable)
/etc/opt/cisco-vpnclient/Certificates (group bin readable)
* You may wish to change these permissions to restrict access to root.
* You must run "/etc/init.d/vpnclient_init start" before using the client.
* This script will be run AUTOMATICALLY every time you reboot your computer.
[root@localhost vpnclient]# /etc/init.d/vpnclient_init start
Starting /opt/cisco-vpnclient/bin/vpnclient: Done
[root@localhost Profiles]# vpnclient connect MacConnect {or McMasterVPN for off Campus (Access from home)}
Cisco Systems VPN Client Version 4.8.00 (0490)
Copyright (C) 1998-2005 Cisco Systems, Inc. All Rights Reserved.
Client Type(s): Linux
Running on: Linux 2.6.16-1.2111_FC4 #1 Sat May 20 19:59:40 EDT 2006 i686
Config file directory:
Initializing the VPN connection.
Contacting the gateway at 130.113.69.8
User Authentication for MacConnect...
Enter Username and Password.
Username []: (your username)
Password []: ***************
Authenticating user.
Negotiating security policies.
Securing communication channel.
For McMaster Authorized Use Only!
Please ensure you have the latest security patches and anti-virus software applied. Virus-infected
computers will be disconnected without notice.
Idle sessions are disconnected after 30 minutes of inactivity.
All sessions are disconnected after 3 hours of continuous use.
For assistance, please contact the Technology Service Desk at (905)-525-9140 Ext. 24357.
Do you wish to continue? (y/n): y
Your VPN connection is secure.
VPN tunnel information.
Client address: 130.113.94.113
Server address: 130.113.69.8
Encryption: 168-bit 3-DES
Authentication: HMAC-MD5
IP Compression: None
NAT passthrough is inactive
Local LAN Access is disabled
I changed /etc/opt/cisco-vpnclient/Profiles/sample.cnf to kai.pcf :
[main]
Description=KAIExtranetClient
Host=210.118.#.#
AuthType=3 <=== change for non-group authentification
and
root@satellite:~ # vpnclient connect kai
Cisco Systems VPN Client Version 4.8.00 (0490)
Copyright (C) 1998-2005 Cisco Systems, Inc. All Rights Reserved.
Client Type(s): Linux
Running on: Linux 2.6.15-26-686 #1 SMP PREEMPT Thu Aug 3 03:13:28 UTC 2006 i686
Config file directory: /etc/opt/cisco-vpnclient
Enter Certificate password: *****
Initializing the VPN connection.
Secure VPN Connection terminated locally by the Client
Reason: Failed to establish a VPN connection.
There are no new notification messages at this time.
Failed again.
so, Tried again on Openswan (IPsec)
root@satellite:~ # cat /etc/ipsec.conf
config setup
interfaces="ipsec0=eth0"
forwardcontrol=no
klipsdebug=none
plutodebug=none
manualstart=
# plutoload=%search
# plutostart=%search
# plutowait=no
conn kai
type=tunnel
auto=start
auth=esp
authby=secret
keyexchange=ike
keylife=1h
keyingtries=1
pfs=yes
left=192.168.209.130
leftnexthop=192.168.209.1
leftsubnet=192.168.209.0/24
right=210.118.#.#
rightsubnet=210.118.#.0/24
root@satellite:~ # cat /etc/ipsec.secrets
# RCSID $Id: ipsec.secrets.proto,v 1.3.6.1 2005/09/28 13:59:14 paul Exp $
# This file holds shared secrets or RSA private keys for inter-Pluto
# authentication. See ipsec_pluto(8) manpage, and HTML documentation.
# RSA private key for this host, authenticating it to any other host
# which knows the public part. Suitable public keys, for ipsec.conf, DNS,
# or configuration of other implementations, can be extracted conveniently
# with "ipsec showhostkey".
: RSA /etc/ipsec.d/private/satelliteKey.pem
192.168.209.130 210.118.126.201 ""
root@satellite:~ # ipsec setup start
ipsec_setup: Starting Openswan IPsec 2.4.4...
ipsec_setup: insmod /lib/modules/2.6.15-26-686/kernel/net/key/af_key.ko
ipsec_setup: insmod /lib/modules/2.6.15-26-686/kernel/net/ipv4/xfrm4_tunnel.ko
ipsec_setup: insmod /lib/modules/2.6.15-26-686/kernel/net/xfrm/xfrm_user.ko
root@satellite:~ # ipsec look
satellite Tue Aug 8 15:45:43 CDT 2006
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 192.168.209.1 0.0.0.0 UG 0 0 0 eth0
192.168.209.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
210.118.126.0 192.168.209.1 255.255.255.0 UG 0 0 0 eth0
Failed again !!!!
** note that ipsec port 500 is used by another program.
root@satellite:~ # lsof -i:500
COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME
vmnet-nat 4548 root 6u IPv4 11693 TCP *:isakmp (LISTEN)
vmnet-nat 4548 root 7u IPv4 11694 UDP *:isakmp
in this case, you should close the vmware nat.
root@satellite:/etc/vmware/vmnet8/nat # /etc/init.d/vmware stop
Stopping VMware services:
Virtual machine monitor done
Bridged networking on /dev/vmnet0 done
DHCP server on /dev/vmnet1 done
Host-only networking on /dev/vmnet1 done
DHCP server on /dev/vmnet8 done
NAT service on /dev/vmnet8 done
Host-only networking on /dev/vmnet8 done
Virtual ethernet done
[main]
Description=KAIExtranetClient
Host=210.118.#.#
AuthType=3 <=== change for non-group authentification
and
root@satellite:~ # vpnclient connect kai
Cisco Systems VPN Client Version 4.8.00 (0490)
Copyright (C) 1998-2005 Cisco Systems, Inc. All Rights Reserved.
Client Type(s): Linux
Running on: Linux 2.6.15-26-686 #1 SMP PREEMPT Thu Aug 3 03:13:28 UTC 2006 i686
Config file directory: /etc/opt/cisco-vpnclient
Enter Certificate password: *****
Initializing the VPN connection.
Secure VPN Connection terminated locally by the Client
Reason: Failed to establish a VPN connection.
There are no new notification messages at this time.
Failed again.
so, Tried again on Openswan (IPsec)
root@satellite:~ # cat /etc/ipsec.conf
config setup
interfaces="ipsec0=eth0"
forwardcontrol=no
klipsdebug=none
plutodebug=none
manualstart=
# plutoload=%search
# plutostart=%search
# plutowait=no
conn kai
type=tunnel
auto=start
auth=esp
authby=secret
keyexchange=ike
keylife=1h
keyingtries=1
pfs=yes
left=192.168.209.130
leftnexthop=192.168.209.1
leftsubnet=192.168.209.0/24
right=210.118.#.#
rightsubnet=210.118.#.0/24
root@satellite:~ # cat /etc/ipsec.secrets
# RCSID $Id: ipsec.secrets.proto,v 1.3.6.1 2005/09/28 13:59:14 paul Exp $
# This file holds shared secrets or RSA private keys for inter-Pluto
# authentication. See ipsec_pluto(8) manpage, and HTML documentation.
# RSA private key for this host, authenticating it to any other host
# which knows the public part. Suitable public keys, for ipsec.conf, DNS,
# or configuration of other implementations, can be extracted conveniently
# with "ipsec showhostkey".
: RSA /etc/ipsec.d/private/satelliteKey.pem
192.168.209.130 210.118.126.201 ""
root@satellite:~ # ipsec setup start
ipsec_setup: Starting Openswan IPsec 2.4.4...
ipsec_setup: insmod /lib/modules/2.6.15-26-686/kernel/net/key/af_key.ko
ipsec_setup: insmod /lib/modules/2.6.15-26-686/kernel/net/ipv4/xfrm4_tunnel.ko
ipsec_setup: insmod /lib/modules/2.6.15-26-686/kernel/net/xfrm/xfrm_user.ko
root@satellite:~ # ipsec look
satellite Tue Aug 8 15:45:43 CDT 2006
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 192.168.209.1 0.0.0.0 UG 0 0 0 eth0
192.168.209.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
210.118.126.0 192.168.209.1 255.255.255.0 UG 0 0 0 eth0
Failed again !!!!
** note that ipsec port 500 is used by another program.
root@satellite:~ # lsof -i:500
COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME
vmnet-nat 4548 root 6u IPv4 11693 TCP *:isakmp (LISTEN)
vmnet-nat 4548 root 7u IPv4 11694 UDP *:isakmp
in this case, you should close the vmware nat.
root@satellite:/etc/vmware/vmnet8/nat # /etc/init.d/vmware stop
Stopping VMware services:
Virtual machine monitor done
Bridged networking on /dev/vmnet0 done
DHCP server on /dev/vmnet1 done
Host-only networking on /dev/vmnet1 done
DHCP server on /dev/vmnet8 done
NAT service on /dev/vmnet8 done
Host-only networking on /dev/vmnet8 done
Virtual ethernet done
No comments:
Post a Comment